- Facebook is littered with frauds, bots, and hackers looking to take advantage of unsuspecting users.
- You might wonder what someone would even want with your Facebook account.
- There are reasons and ways you can counteract these attacks.
Get help by ordering the immediate help package for $149. Guaranteed refund.
Can't afford it? Order Priority Help for $39.95 here.
If you’ve used Facebook for more than a couple of years, you’ve undoubtedly gotten a strange message from a friend at some point. It’s not in their usual ‘voice,’ and it’s asking for you to click on something you don’t recognize.
Your friend has likely been hacked.
And chances are, you’ve been hacked at some point too. How does this happen? Why does this happen? And what can you do to prevent it?
We’ll answer all of these questions in the article below.
In this video I am going to give you all the real information about how Facebook can be hacked.!!! Comment section has been disabled due to uns. Facebook Phishing Script. Please dont use this script to hack someone's ID, I have created this script only to practice when I was learing php back in 2013. Edit doaction.php and replace YOUREMAILADDRESS with the email you want to recieve access. Upload it to a PHP supported web server. I am not recieving antything.
What Does Anyone Want With My Facebook Account?
Hackers can harvest value from your account in a variety of ways.
Phishing is the most common technique used for hacking FB passwords. It is very easy. Open a web browser and head over to the Face Geek website. When you're there, click on the button that says Click here to start to start hacking Facebook accounts. On the following screen, paste the URL of the Facebook account you wish to hack and click on the button that says Hack this Facebook account. 7 Urgent Steps to Take When Your Facebook Account Gets Hacked. Security and hacking issues are rampant in social media. Here are your options for recovery and future protection in case your.
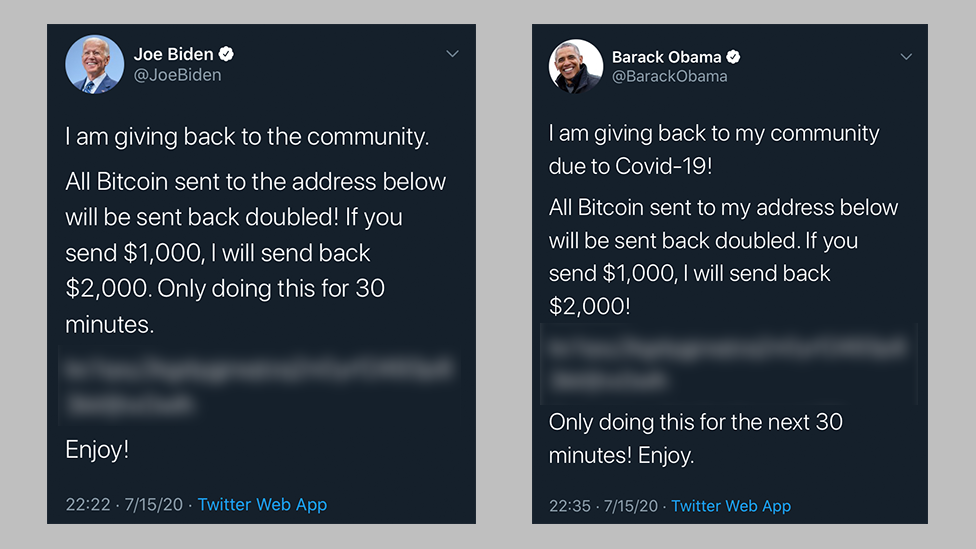
The most simple reason is emotional. Some people are jealous or obsessive, and they want to get an inside look at your account and your messages. They can hire a hacker to infiltrate your account. From there, they can scan your private information or even post something detrimental under your identity.
A complete stranger can also hack you. This is where the shady messages come into play. They can send messages to your friends, baiting them to click on malicious links so they can hack them too.
Hackers can also steal personal information through your Facebook account that can ultimately help them steal your identity. Some people have credit cards, phone numbers, and even social security numbers stored on the platform. They can also find information that can provide answers to security questions, such as your first pet or your mother’s maiden name.
How Do They Do It?
Your account can be breached in a variety of different ways. Here are just a few:
Phishing is still a common way hackers can breach social media accounts. They can set up imposter sites that ask you to ‘log-in,’ but only steal your log-in information. This process often starts with an email containing a link asking you to log-in to your account.
Keylogging is another common tactic for hackers. A keylogger program, which can be set up on your device remotely, records the keys you enter. Key-loggers can record your password information or even your banking information.
Password storage may be helpful when trying to keep track of all of your passwords, but it can make you vulnerable to attack. If a hacker manages to breach your browser’s password manager, they can have a field day with your private information.
Large database breaches are fairly common and can happen to almost any online service. If you have a user on an online service that is hacked, the hackers might try the same password and email you had there on different services. That’s why you should always use a unique password on every online service you use.
Social Engineering is a psychological manipulation where the hacker can pretend they are a friend or a co-worker, and where you are tricked into giving out personal information like a password to a service.
These are just five of the most popular ways hackers can breach your Facebook account, and they’re just the tip of the iceberg. Thankfully, there are ways that you can protect yourself.
How You Can Secure Your Facebook Account
In order to protect your Facebook account, you can start with the following good practices:
- Avoid emails that ask you to log-in to your Facebook account unless you’re 100% certain it’s not an imposter.
- Don’t store your passwords on your browser.
- Always use strong passwords, and avoid the most common mistakes when creating passwords.
- Always log out of your devices.
From there, you can take further steps to secure your Facebook account.
You can activate Two-Factor Authentication. This adds an extra layer of protection that makes it significantly harder for hackers to infiltrate your profile.
You should also avoid accepting friend requests from random people. While it may make you feel popular, these accounts can become unwanted guests that lurch personal information from you with the new access you’ve allowed them.
Likewise, adware and malware bots can do the same. Be sure to install a malware remover onto your computer.
If you’re worried about your Facebook account’s security, you can order a security audit here. If you have already been hacked, you should read our article on how to recover a hacked Facebook account.
Featured image by AFP PHOTO & JOEL SAGET.
Get our Digital Protection Plan
Phishing Facebook Hack

With our Digital Protection plan, we will help you immediately if you have been hacked, had your photos or videos leaked, or if your identity has been misused.
Phishing is the most commonly used method to hack Facebook. The most widely used technique in phishing is the use of Fake Log in Pages, also known as spoofed pages. In this post, you will learn about what is phishing, phishing attack, types, and techniques, how we can prevent such attacks and phishing facebook page.
You Can Also Read
What is Phishing?
It is the most common method used by hackers to hack accounts and an example of social engineering techniques that are used to deceive users. A phishing attack can be used to hack any type of accounts (almost most of the accounts can be hacked using this technique).
Phishing is a fraud and illegal activity used to obtain some bank account credentials, social account username, email address and passwords, credit card and many more fraud activities.
Hackers create a fake phishing page that looks like the original official website and due to this many people enter their information.
Hackers mainly use email messages, Instant messaging platforms like Facebook, WhatsApp, WeChat, Hike, etc. to send the links for hacking your passwords.
In a survey, It is found that phishing is one of the most common techniques used by hackers to hack accounts and the success rate of this technique is high. But nowadays people are getting aware of this techniques but we need to update ourselves from time to time from the latest hacking methods.
Easy Way To Hack A Facebook Account
Suggested: Increase real Instagram followers using this tool for free
Phishing Attack
Code To Hack Facebook Account
The phishing attack is one of the dangerous fraud activities that can steal your important and sensitive information such as credit cards, social accounts, website admin passwords, etc.
A phishing attack can be used for different purposes like hacking facebook account, Instagram account, credit card numbers, bank account information, and for many other purposes.
Facebook phishing scams are widely used and it is the easiest method of hacking someone’s account. These fake login pages look like the original login pages of sites like Yahoo, Gmail, MySpace, etc. The victim is fooled to believe the fake Facebook page to be the real one and enter his/her password. But once the user attempts to log in through these pages, his/her Facebook login details are stolen away.
You can make any type of phishing login page to hack facebook using phishing. It is a criminal offense and illegal activity so don’t try to anyone. You can try this on your own account or system to learn this technique but do not try it on anyone else.
Suggested: WiFi hacking complete tutorial guide – Hack nearby WiFi password using this tool
Types & Techniques of Phishing
Types and techniques that are commonly used in this type of attack.

Social engineering
In this technique, users can be encouraged to open attachment or links send to their email address or on instant messaging. When users open this link or attachment they got infected by a virus or hacked.
Clone phishing
Clone phishing is a kind of phishing attack whereby a genuine, and recently conveyed, an email containing a attachments/link has its substance and beneficiary address taken and used to make a practically indistinguishable or cloned email.
The link inside the email is supplanted with a malevolent form and after that sent from an email address parodied to seem to originate from the first sender.
It might profess to be a resend of the first or a refreshed variant to the first. This strategy could be utilized to turn from a recently tainted machine and addition and a dependable balance on another machine, by abusing the social trust related to the induced association because of the two gatherings accepting the first email.
Voice phishing

Voice phishing is a good example that not all phishing attack requires to create a fake page of a website to get users password and email ID. In this phishing attack, hackers sent a message to your phone that claims to be from the bank, in which it says that you have some problems related to the bank account and you need to dial a customer number (customer number will be given in your message) to fix the problem.
But this message does not belong to the official bank. It is a trap to get your account bank number and password. When the user dials this number (hackers number which users may think official bank number), Hackers told users to enter their account numbers and PIN.
This type of phishing attack is called voice phishing. This phishing attack is done using VOIP.
Suggested: 3 techniques to hide Your IP Address
Spear phishing
In this phishing attack, hackers target specific individuals by collecting personal information and data of the individuals to increase their chances of success.
Other techniques
- Link manipulation
- Whaling
Suggested: 10 Best educational apps for students – Learning apps to Learn new things
How to prevent Phishing attack
1. Unknown mails
Do not open unknown email messages or links.
2. Attachments
Do not click or download any unknown attachment send by someone in your mail. If you know that the file is safe then you can open it.
3. Two-Step Verification (2-Step Verification)
Always use 2 step verification for all of your accounts such as Gmail, Facebook, WhatsApp. Two-step verification protects you from hackers. Even if they successfully hacked your account they can’t log in to your account. They need to enter the digit code which will be sent on your phone.
4. Antivirus
Use good antivirus software, It can help you to protect all your sensitive information by detecting the virus, fraud links, phishing attack, ransomware attack, etc.
Antivirus also protects you when you are doing some online activities. If the antivirus found some potentially dangerous websites that can steal your information. It will automatically block such websites and files from the Internet.
5. Check the URL
Check the URL of the website before entering any information. A phishing page will look like a real one but you can easily identify them by checking the URL.
6. Do not share OTP
Do not share your bank OTP with anyone or do not enter any sensitive information such as bank account number and password over the voice call.
7. Game links
If your friend sends you a link and invited to play a game then before entering any information check that the link URL is real or fake one.
8. Do not login to your social media accounts using Email links
Do not log in to your account social media account using the mail message as it can be a hacking link to trick you and get your password.
You can find more tips to prevent yourself from hacking.
See Also:
phishing is a criminal offense and illegal activity so don’t try to anyone. This tutorial is for educational purpose.
For any help, you can leave a message on the Facebook page.
